Managed detection and response is a newer aspect of information security. However, it is becoming increasingly crucial for businesses seeking a more robust security posture. To get started with MDR, choose an MDR vendor who fulfils your company’s needs while also adhering to data protection and legal regulations. These suppliers can assist firms in improving…
Is Cyberthreat Permanently Solved by SOC Providers?
Traditional SOCs are no longer adequate in the face of escalating cyber threats and alert fatigue. As a result, SOCs are becoming more automated, allowing analysts to focus on more complicated duties rather than mundane ones. In today’s increasingly cyber-threatened climate, many sector executives feel that automation is critical. Furthermore, many corporations provide structured training…
What Is a SOC Provider?
Having a security operation center (SOC) to monitor your network and secure your data is a vital component of a good cybersecurity strategy. To establish one, organizations must recruit security specialists, negotiate and acquire security software and hardware, set up the SOC, and monitor for threats. Organizations may profit from rather than place this responsibility…
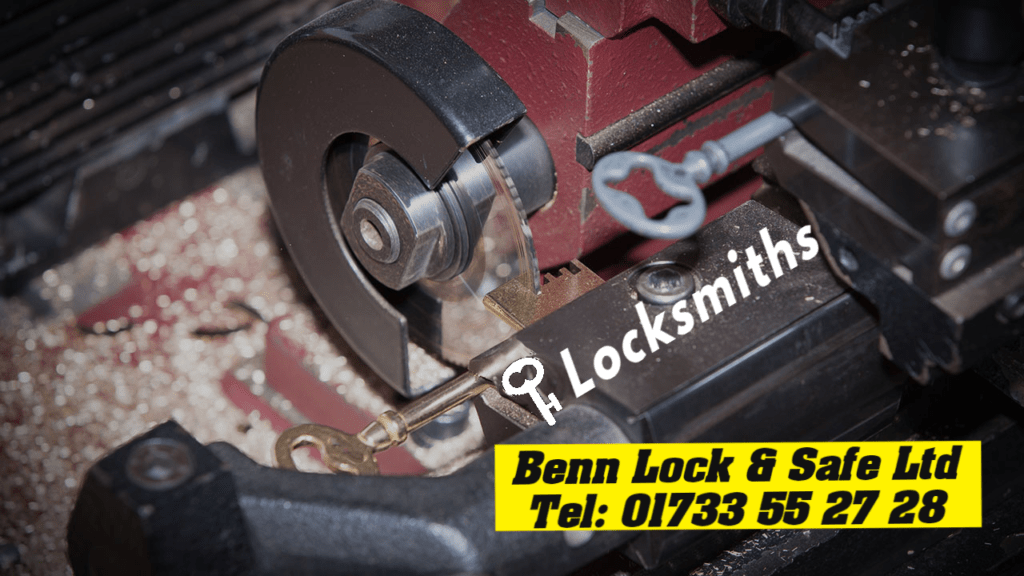
How to choose the best commercial locksmith
How to choose the best commercial locksmith How to Select the Most Reliable Commercial Locksmith Since 1977, Benn Lock and Safe Ltd has provided locksmith services to Peterborough residents and businesses. During that period, we have served hundreds of customers and witnessed the changes that have occurred in our city. We are proud of our…
SOC – What Are the Services They Offer?
As the human element in security grows more critical, many security officials are turning to SOC operators who can personally evaluate and mitigate risks. SOC operators handle existing risks and detect developing threats while satisfying client needs and risk tolerance levels. While technology can halt simple assaults, human analysis is required when a major catastrophe…
Managed SOC – Its Importance in Cybersecurity
Managed SOC is one of the most effective solutions to safeguard your company and ensure compliance with cybersecurity standards. It may solve a wide range of security concerns, such as monitoring operations, incident response, and compliance needs. It may also help safeguard your firm from identity theft. There are several advantages to employing managed SOC…
Best locksmith services in Peterborough.
Best locksmith services in Peterborough. Peterborough’s best locksmith services. Benn Lock and Safe Ltd, Peterborough’s premier locksmith service, provides the best locksmith service. To provide a comprehensive emergency locksmith service, we have developed a dedicated service team. Benn Lock and Safe Ltd is the main provider of emergency locksmith services in Peterborough and the surrounding…
How to protect yourself from Break in attempts
How to protect yourself from Break in attempts The quantity of break-in attempts in this day and age indicates that you must defend yourself. This implies you’ll need reliable locks, security systems, and CCTV guidance. Benn Lock and Safe Ltd, 13 St. Davids Square, Fengate, Peterborough, solely provides expert home security installations. Professional installation firms…
VPN for Public WiFi Security – Public WiFi Can be Dangerous
VPN for Public WiFi Security – Will It Safeguard You? VPNs for public WiFi security: Coffee shops, airports, and supermarkets have public WiFi hotspots. Many individuals are unaware that using public WiFi networks to connect to the internet might drastically damage your online security. You’ve heard of VPNs (Virtual Private Networks) and their myriad security…
What Are Qr Codes, and How Safe Are They to Use
What Are Qr Codes, and How Safe Are They to Use QR codes are defined and explained in detail. The abbreviation QR stands for “quick response.” What Are QR Codes and How Safe Are They to Use: Despite their apparent simplicity, QR codes can store a significant amount of data. The name “Quick Response Code”…